Confidentiality Requirement
Confidentiality Requirement
Preventing data worth protecting from being accessed by unauthorised persons
The means selected to protect data from being accessed by unauthorised persons consists in encrypting the data requiring protection. A wide range of products is available for this purpose in the form of either commercially or freely available software. Not only saved data (e.g. files on hard discs) can be encrypted but also data that are intended for transmission to other persons or computers (e.g. e-mails). In addition, there exist special encryption programmes that even provide a secure transmission channel. When logging in to a remote computer, the user name and password may be read by anyone. This is no longer possible when using a secure transmission channel. The processes underlying encryption are considered secure enough to make code breaking impossible within a reasonable period of time using the technical means available. This is generally known as a secure encryption process.
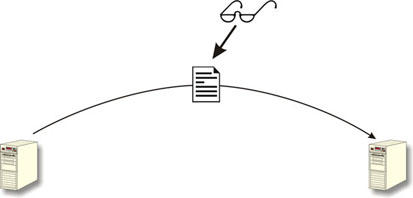
Unencrypted transmission of a document via e-mail, for instance.
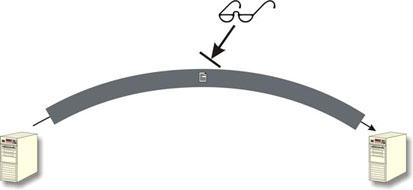
Transmission of a document over an encrypted link.