Integrity Requirement
Integrity Requirement
Integrity and Completeness of Data
The programmes used for protecting confidentiality, nearly always also provide the tools required to ensure data integrity. To protect a document from being tampered, a so-called checksum is generated by means of a mathematical process. The checksum is virtually unique, i.e. the probability that the same checksum is obtained for a different document is small enough to be neglected. In addition, even the slightest modification of the document will result in a completely different checksum. The document together with the respective checksum is then sent to the addressee. The addressee generates the checksum for the document received. If both checksums, the one generated by the addressee and the one transmitted by the sender, are the same, the document was not tampered. In order to ensure that the document is not manipulated together with the checksum in the course of transmission, the checksum is transmitted in an encrypted mode.
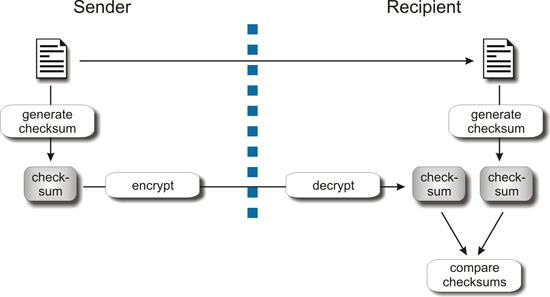
Process chart of a process used to ensure document integrity.